Ransomware attacks are getting more intelligent and more focused as time goes on. The spread of malware has become a widespread and well-known threat to many businesses. Multiple organisations have been hurt by cyber attacks, which have caused some to shut down and put people's lives in danger, especially in the healthcare sector. You can't say enough about how bad these attacks are because they pose a significant risk to the safety and well-being of people and organisations.
whether you are prepared to handle determined individuals keen to obtain bitcoins.?
What is Ransomware?
Ransomware is malicious software that employs cryptovirology to blackmail victims into paying a ransom before releasing or restoring their data. The malware encrypts the victim's files or locks their device until they pay a ransom to unlock them. There are two primary categories of ransomware: those that encrypt the user's data and hold it for ransom and those that prevent the user from accessing their operating system. Moreover, it should be noted that several variations of ransomware can be classified into various categories. There exist multiple primary types of ransomware, encompassing:
Encryptors: An encryptor will encrypt as many of your files as possible, rendering them useless. It is common practice to rename files using a meaningless string of characters or to rename a file using the same name but a different file extension. Suppose a victim can detect an encryption assault in its early stages. In that case, some of their files may stay unencrypted. Suppose your files have been encrypted by ransomware. In that case, you may find a folder with the encrypted file and a ransom note with payment demands and instructions for payment in its place.
Lockware: A form of malicious software that effectively prevents access to computer systems. Typically, the user receives a ransom note that includes guidance on how to make the payment. However, some less advanced versions of lockware do not encrypt files, allowing users to retrieve them. Lockware is often spread through spam emails or phishing links on personal computers. The Trojan used in ransomware assaults often masquerades as a harmless file in an email attachment, deceiving unsuspecting users into downloading and opening the malware.
Scareware: Scareware is a cyberattack that deploys deceptive tactics to coerce individuals into divulging their funds through fraudulent pretences. This technique, commonly called "scareware," leverages fear as a manipulation tool to urge individuals to undertake specific actions, such as visiting counterfeit or perilous websites or downloading malevolent software. Scareware has been known to manifest as pop-up advertisements or propagate via unsolicited emails.
Leakware: A tool specific individuals use to obtain confidential information and threaten to disclose it publicly. Typically, these individuals focus on entities of high repute, such as law firms, medical practices, and corporations with valuable trade secrets. These vendors of leakware operate through online platforms in the dark web, where they share the pilfered data and offer unrestricted access to interested parties seeking to obtain it.
It is crucial to acknowledge that new ransomware variants are constantly arising despite the numerous present types.
Cryptovirology
Cryptovirology pertains to using cryptographic techniques to develop highly malicious software, including but not limited to ransomware and asymmetric backdoors. Historically, cryptography and its various applications have mostly had a defensive purpose, offering users privacy, authentication, and security. Cryptovirology utilises a novel approach to cryptography, demonstrating its potential for offensive applications. This tool has the potential to facilitate extortion-driven attacks that result in the loss of information accessibility, compromised confidentiality, and inadvertent information leaking, all of which are generally safeguarded by cryptographic measures.
Learn More:
What Is Cryptovirology? Is It Dangerous? (makeuseof.com)
https://nordvpn.com/cybersecurity/glossary/cryptovirology/
https://dictionary.sensagent.com/Cryptovirology/en-en/
The sophistication of ransomware assaults has increased as threat actors utilise new tactics, techniques, and procedures (TTPs). The implementation of more intricate encryption algorithms, the assimilation of techniques borrowed from other forms of malware, such as worm-like propagation methods, and the deliberate targeting of specific organisations or groups were all involved in this process.
The Stuxnet computer worm has gained widespread recognition for its exceptional complexity and advanced malicious capabilities. It surpasses the size of a typical computer virus by approximately 50 times, making it a remarkable feat of engineering.
It's important to realise that these harmful programs don't require advanced technology to be created. They exploit weaknesses within your operating system instead. By manipulating the logic and commands within the system, they can carry out destructive actions or engage in malicious activities. These code snippets aren't new or revolutionary but rely on exploiting operating system weaknesses to achieve their goals.
Analysing Stuxnet from a Forensic Perspective
The video has been made available by Stanford University.
To gauge their ransomware risk, organisations must thoroughly evaluate current trends, pinpoint vulnerabilities within their systems, and prioritise implementing effective security measures. This approach is essential in ensuring the safety of valuable data and information and maintaining critical business operations. By taking a proactive stance towards cybersecurity, businesses can effectively safeguard themselves against the growing threat of ransomware attacks.
Developing and updating incident response plans requires a crucial understanding of the current ransomware issues. To enhance their readiness for ransomware attacks, organisations should clearly understand what they can anticipate, how to contain the attack effectively, and how to swiftly and efficiently recover from it.
Data protection and cybersecurity regulations are present in various industries and regions. Staying informed about ransomware trends is crucial for organisations to ensure regulation compliance. It is essential to comprehend the changing threat landscape to adjust security measures and effectively ensure compliance with regulatory requirements.
Ransomware attacks constantly evolve. Attackers develop new techniques and tactics to bypass security measures. Understanding these changes allows organisations to adapt their defences accordingly. It is essential to regularly update antivirus software, firewall rules, and intrusion detection systems to ensure optimal security.
Being aware of the current state of ransomware threats allows organisations to make well-informed decisions regarding strategies for mitigating risks. One crucial aspect of ensuring the security of an organisation involves:
- Weighing the merits of investing in cybersecurity insurance
- Incorporating supplementary security measures
- Improving employee training programs
By taking proactive measures in these areas, organisations can minimise the risks of potential security breaches and safeguard their valuable assets.
For various reasons, it is essential to comprehend the present trends and concerns regarding ransomware. Knowledge of the most recent developments in ransomware empowers organisations and individuals to take proactive measures to protect themselves against emerging threats. It is of utmost importance to have a comprehensive understanding of how attackers execute their strategies to mitigate the potential risks associated with ransomware attacks effectively. This knowledge will enable you to implement security measures and techniques effectively.
There is a form of ransomware known as BlackCat, developed using the Rust programming language. It is distributed through the Ransomware-as-a-Service (RaaS) framework and was first detected in November 2021. BlackCat has since been used to target multiple sectors and organisations across different regions in Africa, the Americas, Asia, Australia, and Europe.
Note: Before engaging in experimentation, enhancing knowledge, and conducting dissections.
Suppose you're an experienced cybersecurity professional interested in analysing code similar to the BlackCat ransomware. In that case, you can learn more details about the approach to it through the provided link.
Practical experience downloading samples into a secure environment, such as a sandbox, is crucial. Additionally, it is essential to understand low-level reverse engineering tools and know machine language programming. Refraining from analysing any malware in a corporate environment is highly advised.
Leaders and decision-makers within organisations must have a comprehensive understanding of the ransomware threat landscape. This knowledge informs strategic decisions on cybersecurity investments, policies, and practices.
Ransomware poses a significant danger to both individuals and organisations alike. Therefore, it is crucial to educate people about the latest ransomware trends so that they can safeguard their data and devices effectively.
Understanding ransomware trends is crucial for fostering collaboration and promoting information sharing within the cybersecurity community. Sharing threat intelligence and best practices is critical to our collective effort to combat ransomware.
The AIDS Trojan attack in 1989 is considered one of the earliest instances of ransomware. The primary method used to distribute the AIDS Trojan was through the efforts of its creator, Joseph Popp. He sent out approximately 20,000 floppy discs to participants of the World Health Organisation's AIDS conference. The disks were titled "AIDS Information - Introductory Diskettes" and came with an accompanying leaflet. The leaflet warned users that introducing the code on the disk to their computer could cause harm. PC Cyborg Corporation also stated they had the right to seek compensation and damages. When the disk is inserted, a text-based graphic will display and reappear after a reboot. Once activated, the program on the disk would keep track of how many times the computer has been booted.
When the count reaches 90, a malicious program will proceed to conceal the file directories and subsequently encrypt or lock the files. To regain access, the user must remit a payment of $189 to a PO Box located in Panama, which is the property of the PC Cyborg Corporation. It is unclear how many computers were affected by the AIDS Trojan and how much revenue Popp obtained. It is important to note that Popp claimed to donate all proceeds to support AIDS research. However, the risk posed by the AIDS Trojan was minimal as it used symmetric cryptography. In addition, prompt development of tools occurred, facilitating file decryption without necessitating payment.
Ransomware has undergone significant evolution since its early days. At first, ransom demands were only a few hundred dollars, but they have now escalated to millions. Cybercriminals possessed a ransomware blueprint and had access to three crucial pieces of technology Dr. Popp lacked: The World Wide Web is an efficient, high-speed delivery system connecting millions of computers worldwide. Encrypt your files with advanced asymmetric cryptography tools that are virtually unbreakable. A payment platform is available that offers fast transactions, anonymous transactions, and the ability to automate decryption tasks upon payment, similar to Bitcoin.
Put together these elements, and that’s when ransomware took off. For example, in 2006, Archiveus used RSA-1024 to encrypt files, making it impossible to unlock them. Victims were forced to purchase items from an online pharmacy to receive the decryption password. In 2008, with the invention of Bitcoin, ransomware attackers could now create unique payment addresses for each victim, thus becoming the preferred payment method. Ransomware attacks have continued to evolve as threat actors continually seek ways to expand the scope of their operations and increase profitability. The ransomware-as-a-service (RaaS) model became popular because affiliates enable ransomware operators to attack more victims with little effort.
There has been a recent increase in ransomware attacks, with numerous high-profile incidents gaining significant media attention. There have been several notable ransomware attacks in recent history, including:
WannaCry: The WannaCry ransomware attack affected 200,000 computers in 150 countries in 2017. The attackers demanded $300 worth of Bitcoin for decryption.
NotPetya: Another significant ransomware attack in 2017 was NotPetya. It rapidly spread through corporate networks, resulting in extensive disruption and damage.
Ryuk: A ransomware strain has been identified as the culprit behind numerous notable attacks, including one in New Orleans in 2019.
REvil: A ransomware group has conducted several high-profile attacks, including targeting the JBS meat processing company in 2021.
Colonial Pipeline: A ransomware attack launched against Colonial Pipeline in 2021 caused extensive disruption and resulted in fuel shortages in several areas of the United States.
BlackCat: Based on a recent publication in the Information Age, several businesses in the Victorian region have fallen victim to a ransomware group known as AlphaV, alternatively referred to as BlackCat. The group has asserted accountability for various attacks targeting companies: pathology company TissuPath, real estate agency Barry Plant, law firm Tisher Liner FC Law, and owners corporation service provider Strata Plan.
An entity has purportedly obtained vast data, measuring 4.95 terabytes, from Barry Plant. In response to the company's refusal to negotiate with them, the group has made the complete dataset available to the public. Among the leaked information are confidential particulars such as email content, non-disclosure agreements, property applications, criminal records, and personal identification belonging to both clients and employees of Barry Plant.
There have been reports of data leaks at TissuPath and Strata Plan. AlphV claims to have leaked the medical records of TissuPath clients. During the incident, TissuPath confirmed that Adversaries exposed patient data such as names, dates of birth, contact details, Medicare numbers, and private health insurance. However, TissuPath has emphasised that the primary database and reporting system, which stores patient diagnoses, was not compromised.
These are just a few examples of the numerous ransomware attacks in recent years. There have been numerous ransomware attacks recently, and the threat only worsens. Suppose you are a professional, student, or researcher in cybersecurity. In that case, reading and gaining a comprehensive understanding of the different types of ransomware that currently exist is beneficial. I have included links to websites, like the one provided, that list a glossary of various types of ransomware.
"Swipe up on this, not that! or Click This, Not That."
Security awareness training is essential for any organisation looking to combat the ever-growing threat of ransomware effectively. It is widely recognised as one of the top three most efficient elements of a comprehensive defence-in-depth strategy. Investing in security awareness training equips your employees with the knowledge and skills necessary to identify and prevent potential ransomware attacks. This proactive approach protects your valuable data and systems. It saves you from the devastating financial and reputational consequences of falling victim to ransomware. Realising the value of security awareness training in fortifying your organisation's defences against this ubiquitous threat is critical. Make it a priority and safeguard your business today. However, we must prioritise the well-being and productivity of our employees by relieving them of the burden of being the frontline defence against phishing attempts.
Imposing the responsibility of frontline defence on employees.
Imagine the impact of an HR employee's job, where they diligently open countless e-mail attachments that flood their inbox daily. Recognising the importance of having these individuals diligently assess every attachment and link is essential. We instruct them to hover their mouse pointer over the link and discover the truth behind its legitimacy or unravel the secrets hidden within the short URL.
Here's an example of a URL that's hidden:
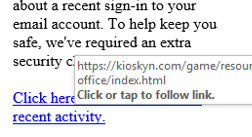
The image is publicly accessible through Washington and Lee University.
Vigilance is crucial in today's digital landscape. By asking these individuals to diligently check for e-mail addresses, obfuscated long or short URLs, grammar, urgency, and other tell-tale signs of scammers and suspicious ransomware behaviour in every e-mail they receive, they become the true frontline defenders of our organisation.
An example of a spam email:
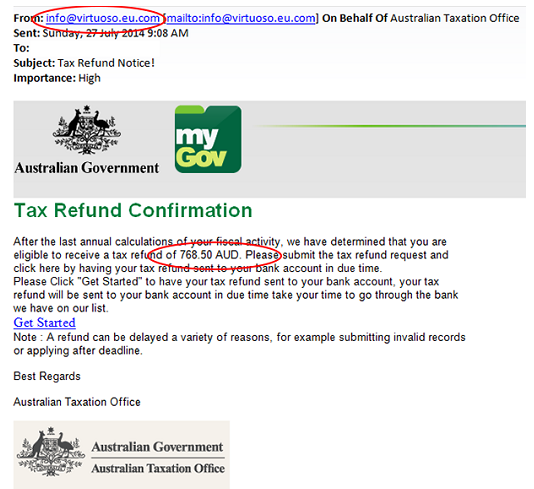
The image is publicly accessible through WAScamNeT
Their attention to detail and commitment to identifying potential threats are paramount in safeguarding valuable assets(Data) and maintaining the security of our organisation and its operations. It is not wise for a company to burden their employees with frontline defence when they have invested significantly in cybersecurity measures.
On July 25, 2017, TrendMicro published a report identifying a new malware delivery method. This method doesn't require the user to click anything to initiate the attack. Instead, the malware infects the computer when the user's mouse pointer hovers over a hyperlink within a PowerPoint presentation slide. The hyperlink can be attached to either text or an image. The attack technique described is ineffective when targeting Microsoft PowerPoint Online or Office 365. This is because these versions need more functionality in their offline/desktop counterparts. Suppose a user of Office 365 should access their account and proceed to open a malicious file using a locally installed application such as PowerPoint. In such a scenario, users may experience negative consequences if their onboard virus protection fails to intercept this specific type of attack.
It is essential to acknowledge that the human workforce is a crucial asset in protecting the front line of a corporation. Phishing education is crucial. However, relying solely on human responsibility for prevention strategies will likely fail. Recent ransomware attacks have highlighted the negative impact of overwhelming employees to defend the front line. We must learn from these critical lessons.
There has been a significant surge in ransomware attacks in recent years, with various industries falling prey to them. According to a report by Dragos Inc., there has been an 87% increase in ransomware attacks targeting industrial organizations in 2022 compared to the previous year. The majority of these malicious software attacks were aimed at the manufacturing sector. In the last year, hackers targeted mining industries in Australia and New Zealand, emphasizing renewable energy companies in the United States and the European Union. Attackers have also intensified attacks on critical sectors like energy, food, water, electrical, mining and natural gas.
According to a recent IBM Security report, ransomware actors deliberately attempted to disrupt global supply chains by targeting the manufacturing sector. This industry experienced the highest number of attacks in 2021, accounting for 23% of all attacks. This marks a significant shift, as the manufacturing sector surpassed the previously dominant financial services and insurance industries regarding attack frequency. Manufacturing organisations have been facing a higher number of ransomware attacks compared to other industries. Attackers have strategically targeted these organisations, anticipating the disruption would have a ripple effect on their downstream supply chains. This pressure would then compel the manufacturing organisations to pay the ransom demanded by the attackers.
Ransomware attacks target various sectors, including education, municipalities, healthcare, infrastructure, finance, banking, utilities, and retail. Cybersecurity experts have recorded that over half of these attacks are aimed at the banking, utilities, and retail industries. It is worth noting that all sectors are susceptible to ransomware attacks.
Some cybercriminals use a technique called double extortion ransomware. They encrypt the victim's data and demand ransom payment within a specific time limit. If the victim doesn't comply with the demands, there's a risk of data theft. The cybercriminals may also share the stolen data with the public, damaging the victim's reputation. It could also give competitors an unfair advantage by allowing them to access confidential information. This creates unnecessary pressure on the victim to pay the ransom.

The Maze ransomware strain in November 2019 marked the first high-profile case of double extortion ransomware. The gang targeted Allied Universal, a security services firm based in California. However, the firm refused to meet the group's ransom demand of 300 Bitcoins, equivalent to approximately $2.3 million. The Maze hackers recently raised their ransom request by 50% and disclosed 10% of the information they obtained. Additionally, they have warned that they might employ data stolen from Allied Universal for a spam operation.
Subsequently, there has been an increase in the utilisation of double extortion ransomware. Based on the findings of CipherTrace's research, there has been a significant surge in double extortion ransomware assaults throughout 2021, exhibiting a substantial growth of over 500%. Moreover, the frequency of these attacks has witnessed a notable quarterly escalation of nearly 200%. The increase in popularity of this phenomenon can be attributed to the capability of this method to empower financially driven hackers to escalate the intensity and coercion on organisations, compelling them to pay exorbitant fees to regain control over their data.
Brenntag, a prominent distributor of chemicals, was the target of a high-profile double extortion attack during the spring of 2021, which was conducted by the DarkSide group and resulted in a devastating ransomware assault against the company. These incidents serve as a clear indication of the threat posed by double extortion ransomware in recent times.
RaaS
Ransomware-as-a-Service (RaaS) is a novel and perilous model transforming the cybercrime landscape. It enables criminal masterminds to lease or vend their sophisticated ransomware to other perpetrators, facilitating the launching of devastating attacks more efficiently and speedily. This model continually evolves and advances, setting new benchmarks in illicit activities. Some RaaS operations even offer exceptional customer service and technical support to their "clients." It is undoubtedly a game-changer and a reminder of the significance of remaining vigilant against cyber threats.
An example of a sophisticated Ransomware-as-a-Service (RaaS) operation is REvil, also known as Sodinokibi. REvil operates on a Ransomware-as-a-Service (RaaS) model, in which the developers lease out the ransomware to individuals known as "affiliates" responsible for executing the attacks. The developers receive a portion of the ransom payments. REvil, a notorious ransomware group, has been responsible for several highly publicised attacks in recent years. Notable targets of their attacks include JBS, a meat processing company, and Kaseya, an IT firm.

Image courtesy of Malwarebytes labs.
The REvil or Sodinokibi ransomware attacks were first noted in Asia, where they mainly affected businesses with small and medium-sized assets. However, they have since spread to Europe and are causing a significant impact. This malicious software is created to exploit any weaknesses in servers and essential resources. As it evolves, it adopts new techniques, such as phishing and exploit kits, to achieve its objectives.
Another notable example is GandCrab, one of the first Ransomware-as-a-Service (RaaS) operations to gain significant attention. GandCrab operated on a sliding scale, meaning affiliates who brought in higher ransom payments were rewarded with a larger share of the profits. This encouraged affiliates to focus on larger organisations and execute more harmful attacks.

Image courtesy of Malwarebytes labs.
These examples demonstrate the increasing sophistication and professionalism of RaaS operations. Additionally, they emphasise the growing danger of ransomware, as these activities empower even individuals with limited expertise to execute harmful ransomware attacks.
Ransomware: An Examination of Associated Challenges
Ransomware attacks can profoundly impact the financial well-being of their victims. They can also have a ripple effect on the global economy. The consequences of these attacks can be severe and long-lasting, making it essential for individuals and organisations to take proactive steps to protect themselves against this growing threat.
In May 2021, the Colonial Pipeline, which transports petrol and jet fuel from Texas to the East Coast of the United States, was targeted by a ransomware attack. Consequently, the pipeline was closed for several days, leading to a shortage of petroleum in several states.
DarkSide, a criminal organisation, was liable for the ransomware attack. They offer ransomware as a service (RaaS). It gives other thieves access to the ransomware software, which they then employ to attack their targets. RaaS groups frequently operate remotely, making it challenging to find and prosecute them.
The attack on the Colonial Pipeline served as a significant wake-up call for the American government and commercial sector. It brought attention to how susceptible vital infrastructure is to ransomware assaults. Following the assault, the US government passed new laws to strengthen critical infrastructure cybersecurity.
The Colonial Pipeline attack significantly impacted the economy. The pipeline shutdown resulted in increased petrol prices and the disruption of supply chains. The episode also resulted in a state of widespread panic, with people hurriedly rushing to fill their petrol tanks. The organisation expended $4.4 million to regain access to its system following the attack. Nevertheless, the overall expenses incurred were significantly more significant, considering the loss of revenue and damage to the organisation's reputation.
Another instance to consider is the WannaCry ransomware assault in 2017, which impacted over 200,000 computer systems across 150 nations. The attack above resulted in extensive disruption, compelling numerous businesses to cease operating their systems. The WannaCry attack is estimated to have caused billions of dollars in financial damage.
Every year, ransomware attacks result in significant economic losses, reaching billions globally. According to Cybersecurity Ventures, ransomware costs are expected to increase to $20 billion worldwide in 2021, compared to $11.5 billion in 2019 and $8 billion in 2018. Around 73% of companies experienced a ransomware attack in 2022, and the global cost of ransomware will be predicted to surpass $30 billion in 2023. Moreover, the average ransomware attacker demands $1.5 million in 2023.
Recovering data after a ransomware attack can be complex due to the advanced encryption algorithms used by modern ransomware. Without the key held by the attacker, it may be impossible to decrypt the encrypted data. This can pose significant challenges for victims trying to recover their data.
Ransomware attacks often use robust encryption algorithms to encrypt the victim’s data. Some of the most commonly used encryption standards in ransomware attacks include:
- AES (Advanced Encryption Standard): AES is a widely used symmetric encryption algorithm considered very secure. Ransomware attackers often use it to encrypt the victim’s data.
- RSA: RSA is an asymmetric encryption algorithm commonly used in ransomware attacks. It allows the attacker to generate a public and private key, with the public key used to encrypt the data and the private key required to decrypt it.
- Salsa20: Salsa20 is a stream cipher used by some ransomware variants, including the Petya and NotPetya strains.
In instances of ransomware attacks, it is common for cybercriminals to employ a variety of encryption standards. The specific encryption algorithm utilized may vary depending on the type of ransomware used and the preferences of the attacker.
One of the obstacles in recovering data from a ransomware attack is that the attackers frequently employ tactics that make data retrieval more difficult. Some ransomware versions may delete or overwrite backup files, which complicates the victim's ability to restore their data from a backup. Additionally, bad actors often threaten to expose or sell illegally obtained information to put more pressure on their targets to comply with ransom demands.
In numerous instances, entities have encountered difficulties restoring their data after a ransomware assault, garnering significant attention and scrutiny. In 2019, the city of Baltimore had a ransomware assault, which substantially disrupted its computer systems for several weeks. The municipal authorities declined to comply with the ransom demand. Instead, they sought to restore their data by utilising backup systems. Nevertheless, implementing this procedure proved challenging and time-consuming, resulting in a prolonged period during which numerous urban services remained inaccessible.
In a separate incident in 2020, the University of California San Francisco (UCSF) experienced a ransomware attack, resulting in data encryption on multiple servers. The university decided to remunerate the assailants $1.14 million to restore access to its data.
The following examples demonstrate organisations' challenges when attempting to recover their data following a ransomware attack. Organisations require comprehensive backup and disaster recovery strategies to mitigate the potential consequences of a ransomware attack.
The Psychological Harm Caused by Ransomware Attacks on Individuals and Organisations
Ransomware attacks may result in considerable psychological repercussions for both individuals and organisations. Such effects may encompass heightened stress and anxiety levels, as well as feelings of violation and helplessness. The consequences of these outcomes can be quite severe and should not be taken lightly.
Stress and anxiety
Ransomware attacks can induce significant stress and anxiety levels among individuals, particularly when their data is exposed to potential risks. Users may have concerns regarding the possible loss of critical files, photographs, or documents.
Employees within organisations may encounter elevated stress levels when critical systems are compromised. The source of this stress may arise from apprehensions regarding job stability, the capacity to meet project timelines, and the urgency to address the situation promptly.
In 2020, the University of California, San Francisco (UCSF) suffered a ransomware attack that caused significant damage. According to the UCSF, the perpetrators successfully infiltrated critical information about the research conducted by the academic members of its medical school. The organisation claims that its study on COVID-19 remained unaffected. The researchers were understandably concerned that this loss of information could harm their efforts to fight the pandemic.
The COVID-19 outbreak has led to increased ransomware attacks targeting healthcare organisations, according to the FBI and other government agencies.
The prevalence of ransomware attacks has the potential to significantly impede care delivery by disabling or encrypting vital electronic health records and computer systems. Such attacks can cause significant disruptions and pose a risk to patient safety and healthcare operations' overall integrity. This forces professionals to record care on paper, causing delays or cancellations of surgeries and appointments. Ambulances are redirected from emergency departments, and the damage to practice infrastructure has resulted in some closures rather than rebuilding.
Experiencing a Sense of Violation
When someone falls victim to ransomware, they often feel violated and helpless. This is because their personal information and precious memories, like family photos, are taken without their consent and held for ransom. The intrusion into someone's personal space can cause anger and powerlessness.
Organisations may feel violated when their systems are compromised, mainly if sensitive customer data or proprietary information is accessed and stolen, leading to a decline in trust and confidence.
The 2019 ransomware attack on Baltimore impacted the entire municipality. It disrupted city services and prevented citizens from accessing critical services, raising concerns about government infrastructure security.
Feelings of Helplessness
Ransomware victims may experience a sense of helplessness, particularly in cases where they lack backup solutions or face financial constraints that prevent them from paying the ransom. The emotional distress caused by the inability to regain access to one's data can be significant.
Many organisations may experience a sense of vulnerability when confronted with ransomware attacks, mainly if they do not possess robust cybersecurity measures or well-defined incident response plans. The immense pressure of making crucial decisions while experiencing stress can be overwhelming.
The Colonial Pipeline ransomware attack in 2021 profoundly impacted the company's leadership. The decision to pay a multimillion-dollar ransom was made under intense pressure, highlighting the sense of helplessness organisations face when dealing with such attacks. The ransomware attack focused on the pipeline's billing systems. Colonial temporarily halted fuel flow through the pipeline as a precautionary measure to prevent the spread of malware to other areas of its operations. Several reports following the attack suggested that Colonial shut down the pipeline partly due to customer billing issues.
The incident in question catalysed increased cognisance amongst the American populace concerning ransomware, prompting legislative action from Congress and encouraging federal agencies to enhance their cybersecurity protocols.
Concern for a Recurrence
People who fall prey to ransomware may feel more worried about being targeted in the future, which can increase their anxiety about online safety. Similarly, companies that have been hit with ransomware attacks often worry about future attacks, which can impact their strategies for cybersecurity and how they allocate resources.
In 2017, Maersk, a prominent global shipping company, experienced a cyber attack known as the NotPetya ransomware incident. The episode mentioned above resulted in significant disruption on a large scale. The three-day interruption of tracking operations and logistics resulted in substantial shipping delays. Nearly 50,000 infected endpoints were identified, with numerous applications and servers impacted across 600 sites in 130 countries. In response, Maersk made substantial investments in cybersecurity measures, motivated by concerns of a potential recurrence.
Effect on Employee Morale
Ransomware attacks can lower workplace morale as employees may feel demoralised by the disruption and pressure to resolve the situation. Additionally, losing trust in leadership's ability to protect data can negatively affect morale.
The ransomware attack in Atlanta in 2018 had a discernible effect on the overall workplace morale within the city government. The employees expressed frustration and demoralisation resulting from the consequences of the attack.
Ransomware attacks can have severe financial and operational consequences and lasting psychological effects on individuals and organisations. Even after the technical aspects of the attack have been resolved, the psychological impact can continue. Therefore, providing adequate support systems for affected individuals and employees within involved organisations is crucial.
What's the next step?
Prevent Ransomware with Powerful Strategies!
Discover the extraordinary realm of ransomware attack prevention as we delve into a captivating series of posts. Unveiling an arsenal of potent strategies, we equip you with the knowledge and tools to safeguard your digital domain. Prepare to embark on a transformative journey towards fortifying your defences against this insidious threat. Stay tuned for an enlightening exploration like no other.

